| Beware of Phishing (Fraud) |
Learn about a type of fraud called “phishing”, the damage from which has been increasing recently, including the methods and knowledge to prevent damage from it.
“Phishing”
Recently the word “phishing” has been picked up by newspapers and news broadcasting. You may have heard or seen it.
“Phishing” is a kind of fraud that is defrauding people of their personal information such as credit card information by using forged emails or forged web pages that look like genuine web pages. The damage is that credit cards are being used and that money is being withdrawn from the bank account using the stolen credit card information or passwords.
(Note) “Phishing” appears to come from “fishing” originally, but it is spelled “phishing”.
What is the actual method of “phishing”?
First, you will receive an email requesting your immediate action. In the email, there is a message indicating that you will incur a significant loss unless you carry out the action written in the email immediately. In the most of the cases, the action is to access a web page and enter personal information such as a password or credit card number.
The email shown below is an example of this.
The email is from “Kumakuma Card Company” and tells you to access immediately the URI on the email, or your credit card may be wrongfully used by someone else.
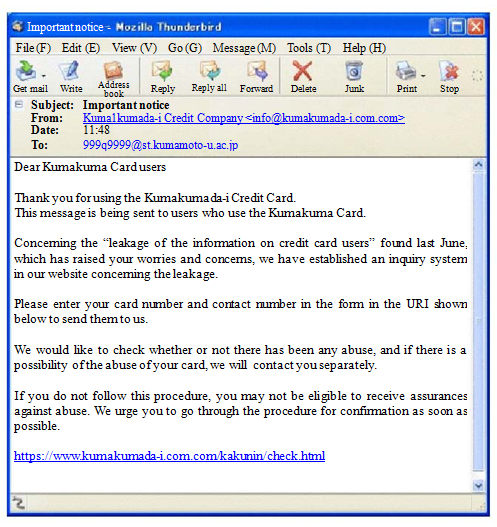
(Note) This email is fiction, just created for this lecture.
You may feel a little doubtful as to whether it is true or not, but as the URI is familiar to you, you clicked the URI. Then, you jump to the web page shown below.
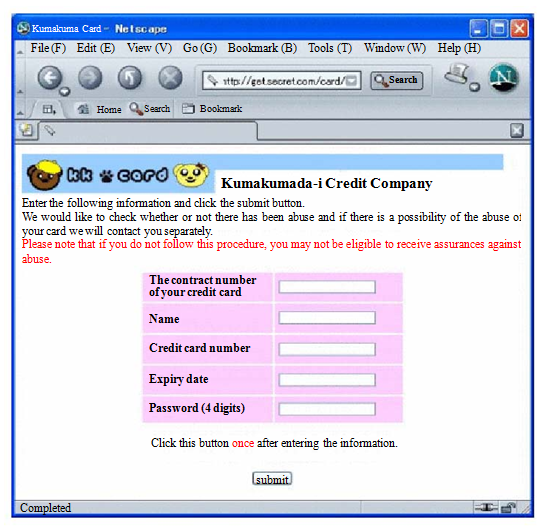
If the image on the web page is the logo mark of “Kumakumada-i Credit Company” that you are familiar with, don’t you think you may think it is true, enter all the required information, and click the “submit” button?
However, it is a completely fake web page, by the time you realize the truth your credit card has already been used by someone else.
Measures to Prevent “Phishing”
The methods of “phishing” are briefly as shown below:
- Fish people by using an email (that is pretending to be a genuine one, but is actually fake)
- Steal information in a web page (that is pretending to be a genuine one, but is actually fake)
- Check whether or not it is a genuine email
- Check whether or not it is a genuine web page
Now let’s see how to check them.
Checking Whether or Not the Email is a Genuine Email
- Check the header of the email
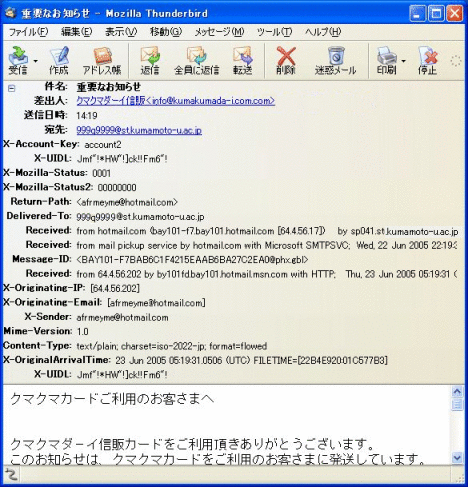
As described in the lectures before, in emails, in addition to the body part you usually read, there is the header part, which includes detailed information such as the communication history.
Seemit, which is developed in the University, has the header information at the top of the body of the email, therefore you can see it just by scrolling through it.
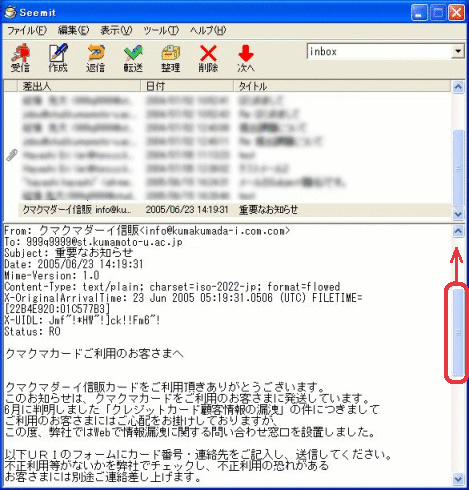

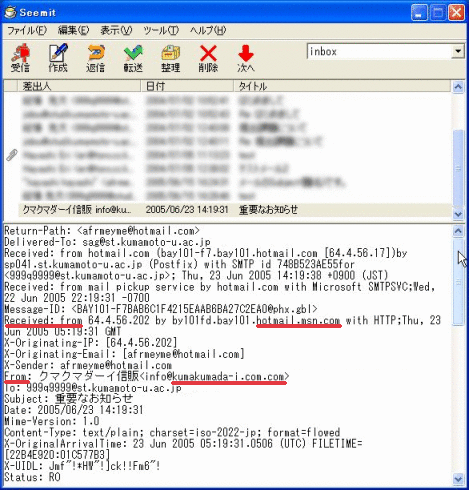
Then, as shown in the figure above, the domain name (on the right of @) in the “From:” field that indicates the sender is
“kumada-i.com.com”, however, the domain name in the “Received:” field that indicates the mail server that actually sent the email is “hotmail.msn.com”.As explained previously, we can see that the fake email is sent wrongly utilizing the fact that the “From:” field that indicates the sender can be modified as you like. If you find such an email, delete it immediately, without hesitating.
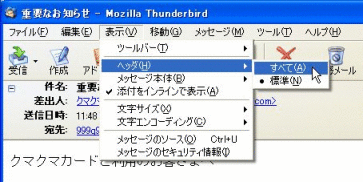
(Note) Mail software other than Seemit
If you use mail software other than Seemit, you can see the header by changing its setting to show the header. The example below is Thunderbird, which has become a major email software application.



- Ask the bank or credit card company directly
If you cannot identify whether it is genuine or not from the header, directly ask the bank or credit card company written as the sender.
However, do not contact the number on the email you received, contact the one written on your bank passbook or card. Otherwise, you may ask about it to a fake company.
Check whether or not the web page is the genuine page
- Check whether or not the URI shown on the email body and the link destination match
The body of “phishing “email always includes the URI of a web page where you are required to enter your personal information. You can open the URI either by copying and pasting it into your web browser, or by clicking the URI, which is the function of email software to execute the web browser automatically and display the link.
If the email is a “phishing” mail, it invites you to go to a forged web page, therefore there must be the URI of the forged web page written in the email. However, if so, most of the recipients will notice that it is fake, therefore, generally the URI shown in the email is a genuine one, but the actual destination of the link to be displayed when you click on it is fake.
For example, in the mail software shown below (Thunderbird), when you put the mouse pointer onto the URI in the body of the email, the (actual) URI that is linked from the URI is shown in the bottom of the window. By checking this, you can identify whether or not the email is a genuine email.
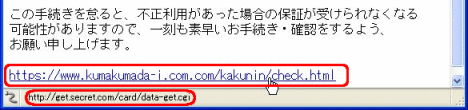
In the example above, the actual destination of the link is “http://get.secret.com/card/data-get. cgi”, which is obviously suspect, so you can see it is strange.
(Note) In the case of Seemit
In Seemit, when the URI is written in the body and the URI has a link (more precisely, it should be an HTML mail, but here we skip the explanation of this), it is shown in the body of the email, so there is no need to put the mouse pointer on it.
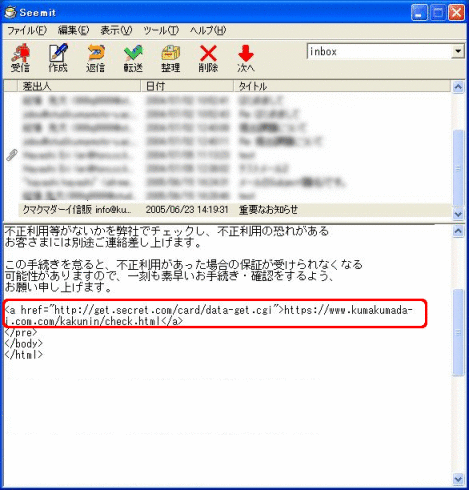
In the figure above, you can see the two URIs are different therefore you can know that the email is suspect.
- Check the URI shown on the top of the browser
You can identify whether or not the web page is genuine to some extent by confirming whether or not the URI shown on the top of the web browser matches the URI written in the body of the email.
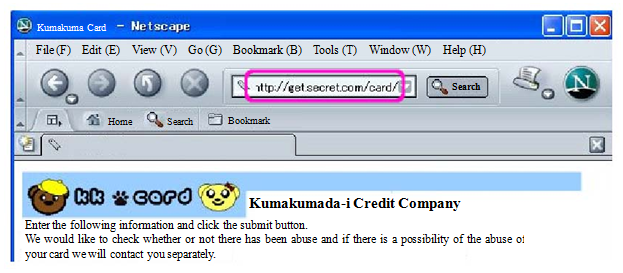
The URI shown in the figure above is obviously suspect.
- Check whether or not the web page is linked from the website of the bank or card company
Check the links of the genuine web page of the bank or card company in order to find out whether or not you can jump to the web page in the email following the links. If it is so urgent that they bothered to send an email to ask you to go to the web page, there must be a notice somewhere near the top page. If you do not find such a notice, it is likely to be a fake.
If you want to confirm whether it is genuine or not, ask the company about it through the contact information written on the top page. Be sure to access the contact information from the genuine web page of the company you have checked, not from the one written in the email.
